TCS HackQuest Season 5 | Round - 1
Hello folks, I’m really excited to share my TCS HackQuest Season 5 journey with you all through this blog !
It was quite amazing journey to be honest to compete with 22 thousand participants from 600+ instituions all across India ! I was one of the top 10 grand finalist of TCS HackQuest Season 5, awarded with 10k INR cash prize & job offer.
So, there were 3 rounds this season which were consisting of CTF challenges, Group Discussion & proctored CTF round (which was the final round.)
Round 1 had time duration of 4 hours in which we were given 10 challenges of different categories (such as Web, Reversing, Forensics, etc..) After solving the round 1 challenges we were given 2 hours to document everything we did to obtain the flag in a word document provided by TCS HackQuest team. So, make sure to write understandable descriptive steps that you have taken to solve the challenges & take screenshots of everything you do !!
I wrote this blog in a very beginner friendly way to help my future infosec buddies !
Following are the 5 challenges that I managed to solve in Round - 1 and got 900 points!
1. Digi Magic
Flag: "hq5{s0_Y0u_KN0W_HoW_$$1_worKs}"
-
As the challenge talked about digital signature, it instantly came to my mind to check for SSL/TLS certificate.
-
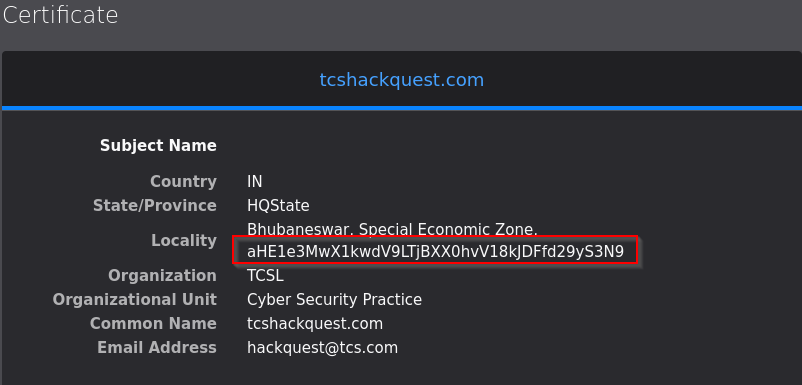
So, I clicked on ‘View Certificate’ option in mozilla firefox browser.
-
There in the Locality field, you will see the base64 encoded string just decode it and you will get the flag.
2. I Am Always
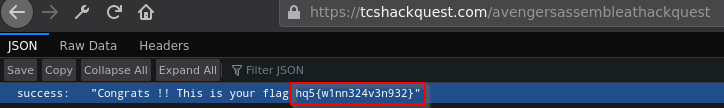
Flag: "hq5{w1nn324v3n932}"
-
As the challenge talked about hidden flag and when I browse through the challenge link, there were multiple images and first thought in my mind was to check for steganography or some sort of EXIF embedding in image metadata.
-
I downloaded all the images from the challenge link.
-
Tools Used: Metapicz
-
I search in all images for EXIF manipulation & found cool endpoint string in metadata of Hulk image.
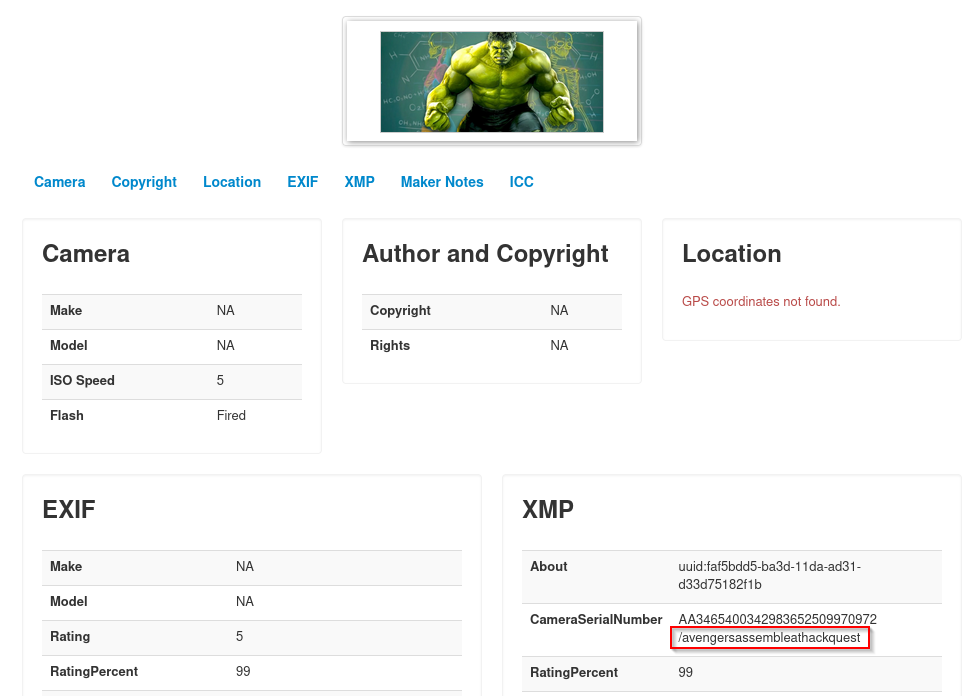
-
Visit this endpoint and you will get the flag !!
3. Ice Cream Dispenser
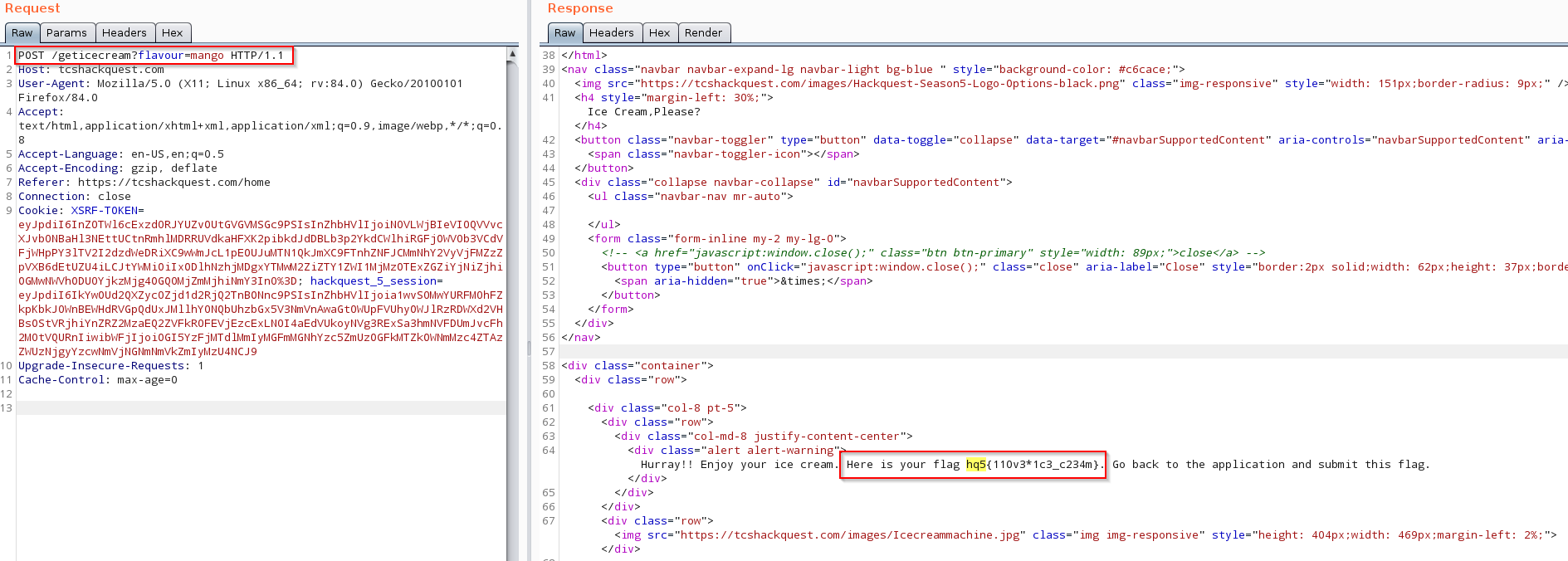
Flag: "hq5{110v3*1c3_c234m}"
- This challenge involved small guess work.
- I intercepted the request in burp suite.
- Request: GET /geticecream
- When I send this request, response came in as – “Missing Flavour”. So, I added flavour parameter with a random string.
- For example: GET /geticecream?flavour=mango. But then again response returned as – “Are you requesting it correctly!”
- Then I change the GET request to POST and guess what the flag was returned in the response.
- Final request: POST /geticecream?flavour=mango
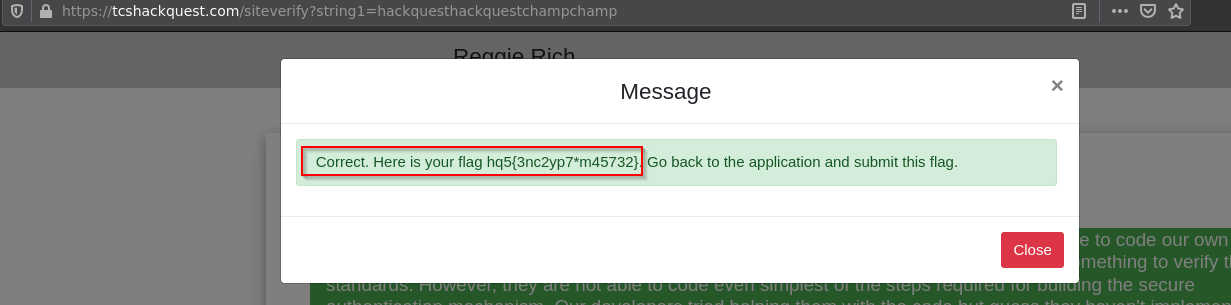
4. Reggie Rich
Flag: "hq5{3nc2yp7*m45732}"
- This challenge was simple code review and bypassing of weak pattern matching function.
- Viewing the source code of the challenge page gives us commented source code at the bottom of the page.
-
Code:
#=> Code: function replace_string($j0){ $a1=$j0; ##hackquestchamp $h2=preg_replace("/hackquestchamp/","",$j0); #replacing with empty string if($a1==$h2) { if(str_contains($h2,'hackquestchamp')) echo "Finally Working ".$h2;} else{replace_string($h2);}} - As you can see it will match the string hackquestchamp & replace it with the empty string.
- So,to bypass this weak pattern matching, simply input the following string.
- Final String: hackquesthackquestchampchamp
-
Pattern matching will remove the middle string ‘hackquestchamp’ completely & then first ‘hackquest’ string gets joined with last ‘champ’ string resulting in function bypass and it returns our flag.
5. Record
Flag: "HQ5{Malware_implement_persistence}"
- This challenge was too time consuming to check through all the logs to identify the flag.
- After clicking on “Take Me To Binary”, a RAR file get downloaded.
- Decompressing it will give two files: App.evtx & system.evtx
- Firstly, I checked what is the file type by running Unix command - file.
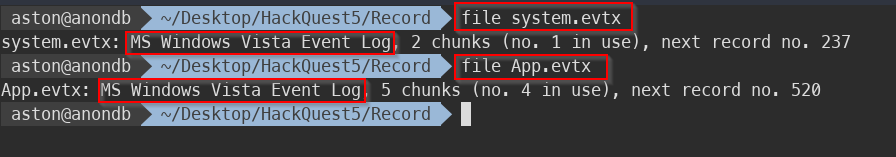
- As you can see in the screenshot, it is the event log file which can be opened by Windows Event Viewer. I immediately open both files and started looking for any intresting logs.
- As the challenge specifically said about “malware”. So, I tried searching record with string such as Trojan, Malware, Ransomware & to my notice I found one ransomware record consisting of based64 encoded string in the system.evtx log file.
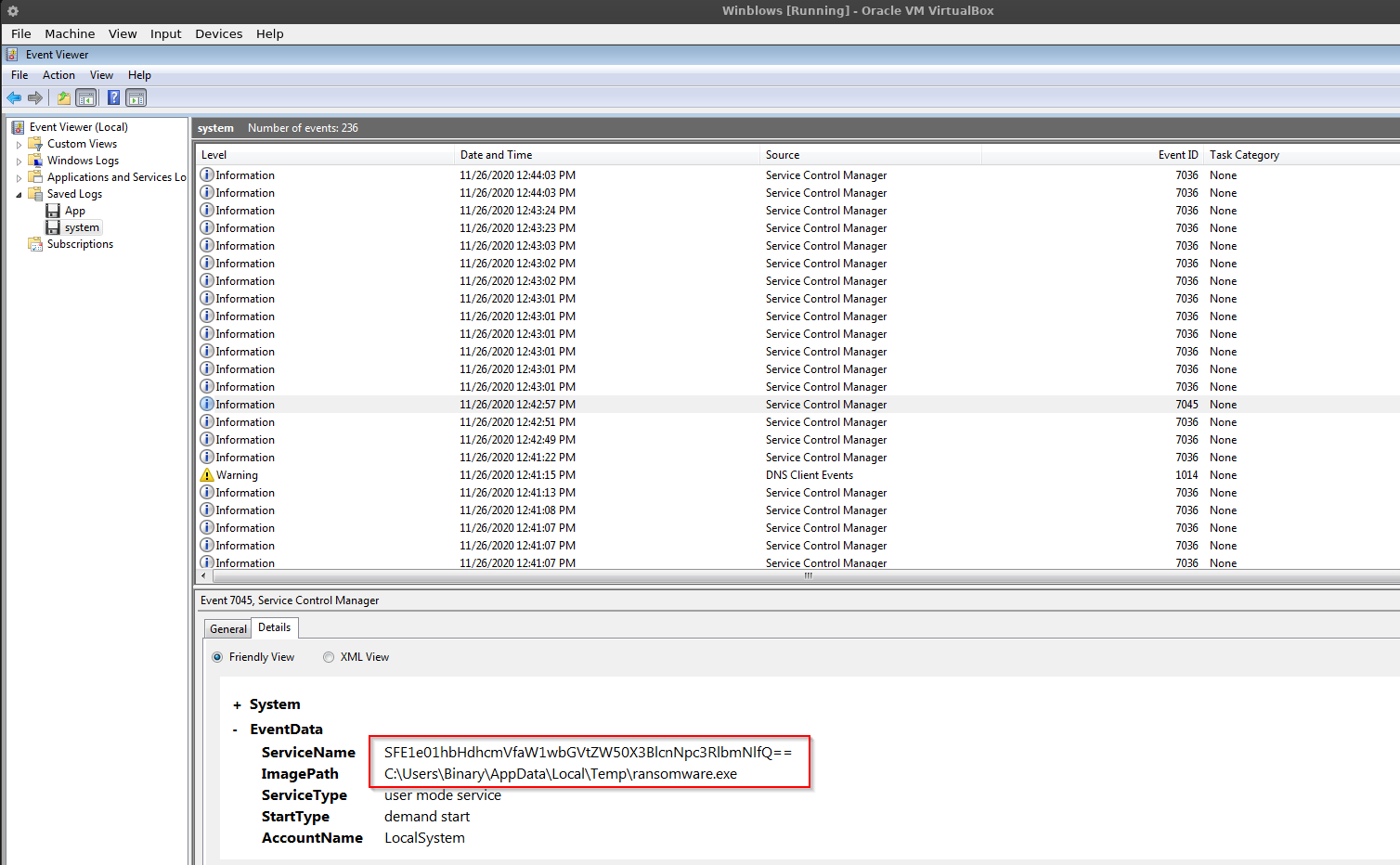
- Decode the string and you will get the flag in plain text.
Gracias !!
 Namaste, I'm Saraunsh Shewale from India <3. I love to hack !. Going to blog about my research in infosec, writups of CTF challenges & HTB machines and occasional life lessons !!
Namaste, I'm Saraunsh Shewale from India <3. I love to hack !. Going to blog about my research in infosec, writups of CTF challenges & HTB machines and occasional life lessons !!