Breaking into Contiinued Ft. Phishing the phishers..!
I know it’s been a long time since I blogged anything as I was busy with lot of things and being lazy at the same time. Now that I’m back, I will try to be more consistent and more frequent to share some more good stuff. So, that it will keep myself and this domain alive! 😁
Disclaimer 101
Before proceeding further, I want my readers to know that this writeup is just for educational purpose. I don’t intend to harm, steal or masquerade someone’s identity. Most of the details are blurred for obvious reasons. This is just to understand how modern threat vectors work and how can we be safe from such attacks!
Let’s go..!
So, recently I recieved an sms on my cell phone which pretends to be from Irish revenue. It is about some delivery for which I need to pay the custom charge. There’s a link in it as well to pay the fees and get my package delivered. Easy right? Well I knew it was fake website by looking at it in the first place but I still had some curiosity to dig deeper into it.
(I can’t help it…it’s not me, it’s my dodgy mind..!).
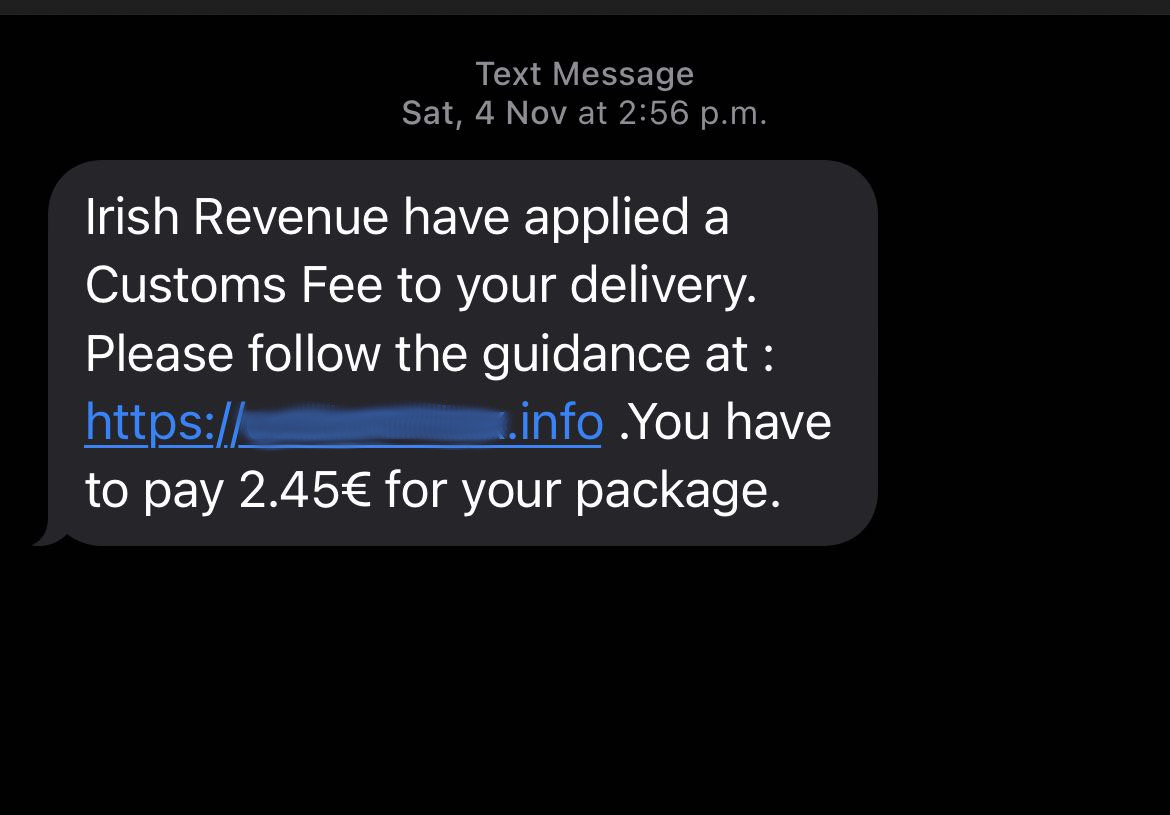
Enum enum and enum!
Visited the link in web browser and it redirected me to a page which exactly looks like famous courier service - An Post. Well, I saw many blog post recently which highlights the usage of An-Post landing page by threat actors to phish the users.
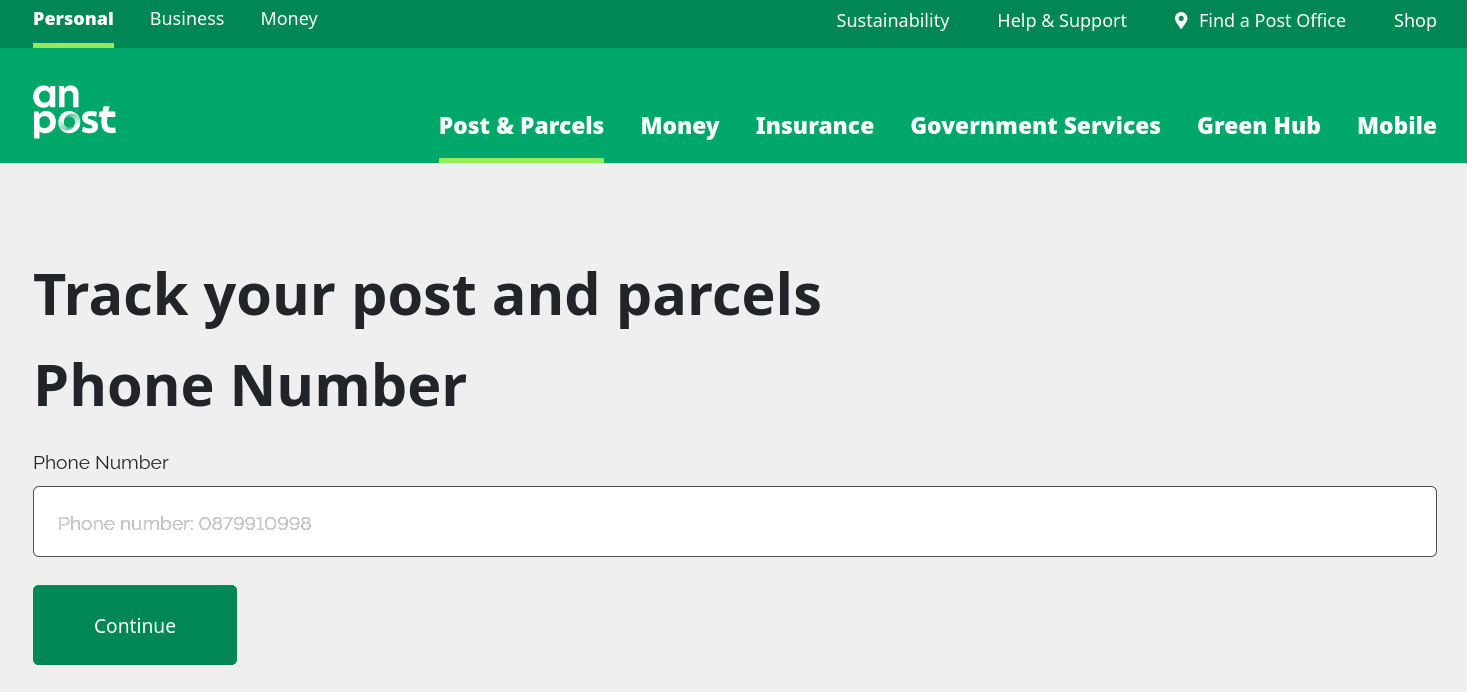
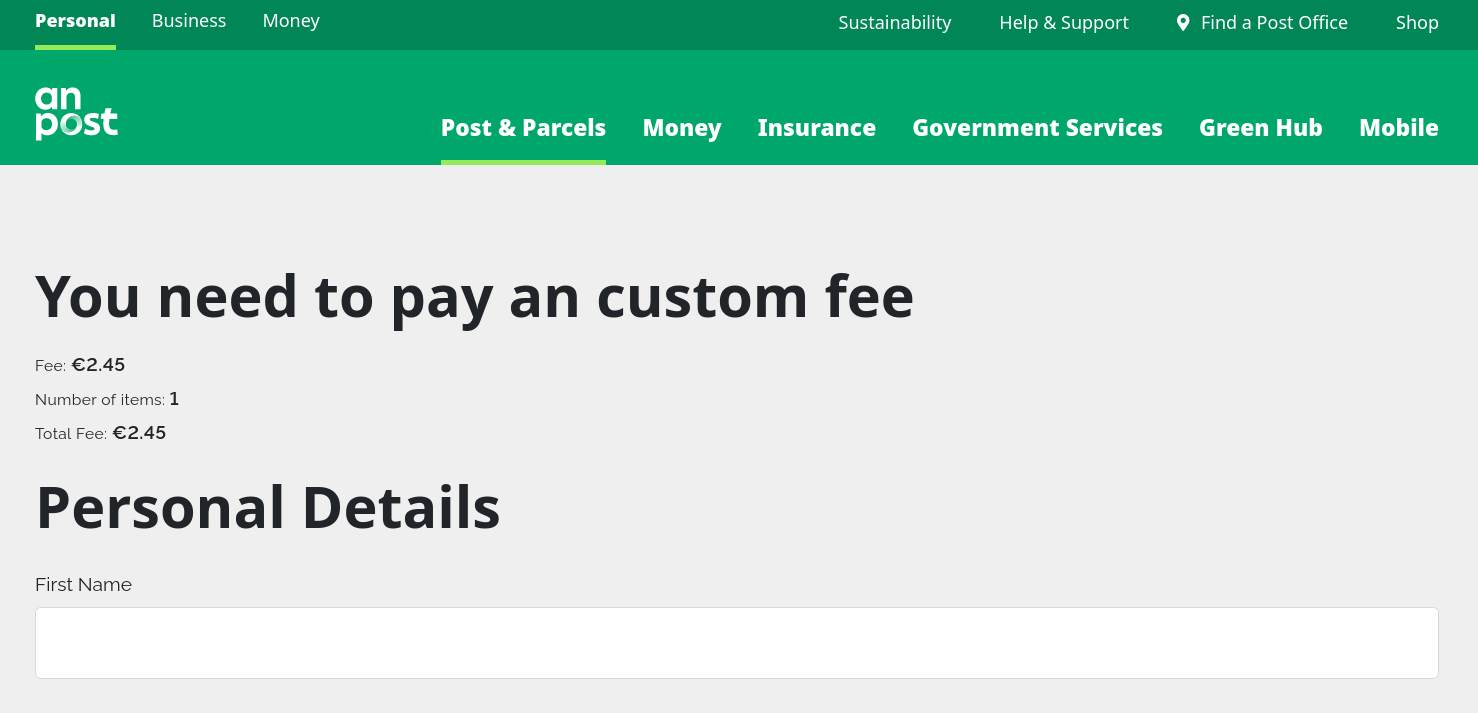
Without hesitating, I turned my burpiee interceptor on and started playing with the web page. Provided dummy details such as phone number, name, address, etc. and later it redirected to payments page which prompted me to enter my credit card details. Yes, afterall this is what they want from me. (They probably didn’t know how broke I’m …!)
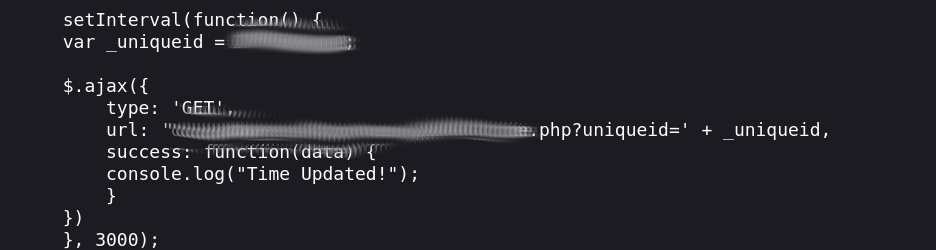
Upon checking burp history, I saw an interesting URL endpoint which keeps on sending GET requests to capture the time (More like a basic C2 component). This was verified by inspecting the client side code.
This endpoint motivated me to perform basic injection attacks like LFI, SQLi, etc and guess what the parameter was not sanitizing the user supplied input and directly passing it to the SQL query. The endpoint was vulnerable to SQL injection and I could easily pwn the database by querying table records.
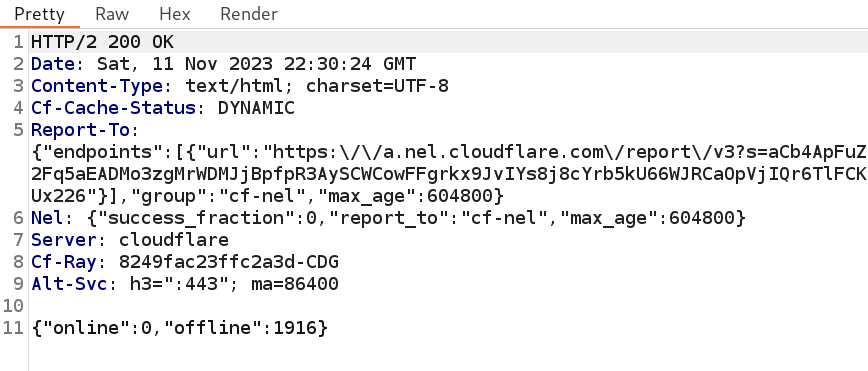
I enumerated the entire database, gathered information related to phishing kit like administrator username, password hash, etc. After general google dorking, I came to find out that, it’s a popular phishing kit known by Contiinued. Although, it’s poorly configured and easy to pwn but still has lot of customizability to target and scam users. I further checked database records and found out hundreds of users got tricked and ended up giving their personal information including credit card details (scary shit!). To be precise, by the time I was investigating, it almost had 1916 records!
Further drillin’ down..!
My dodgy mind still wanted me to see the admin panel of this phishing kit but it was behind password protected endpoint. Just like any other kid, I had a curiosity to know what is behind that wall !
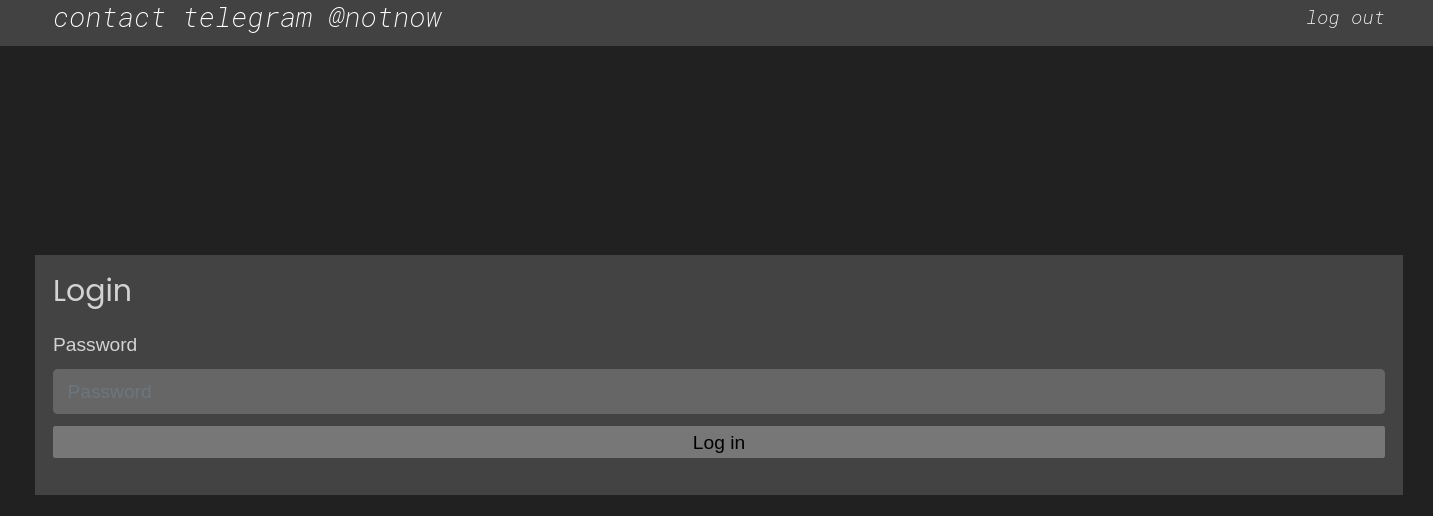
Conducted further test cases to bypass the login functionality but had no luck with it. Then, I started enumerating the hidden directories using my favourite fuzzer a.k.a Gobuster. Found multiple directories which had directory listing enabled as I said previously, it was poorly misconfigured server. The application was vulnerable to IDOR and had poor authorization checks in place which can be easily bypassed.
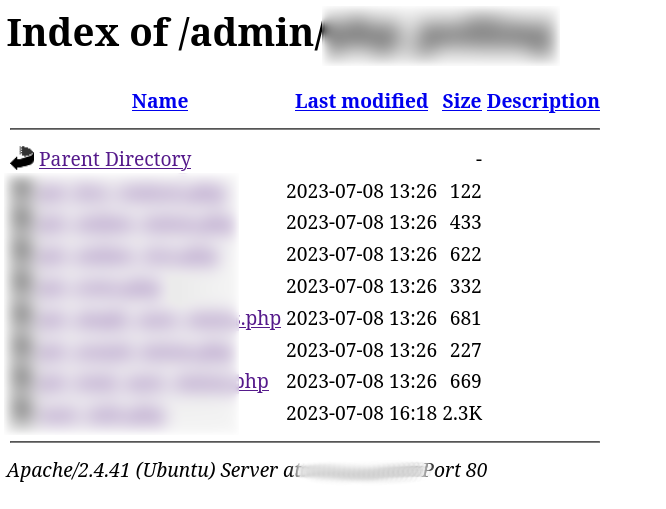
I found one interesting .php file for which I did parameter fuzzing and luckily that parameter resulted me in bypassing the authorization check and thus I was able to directly see the phishing kit’s backend functionality.
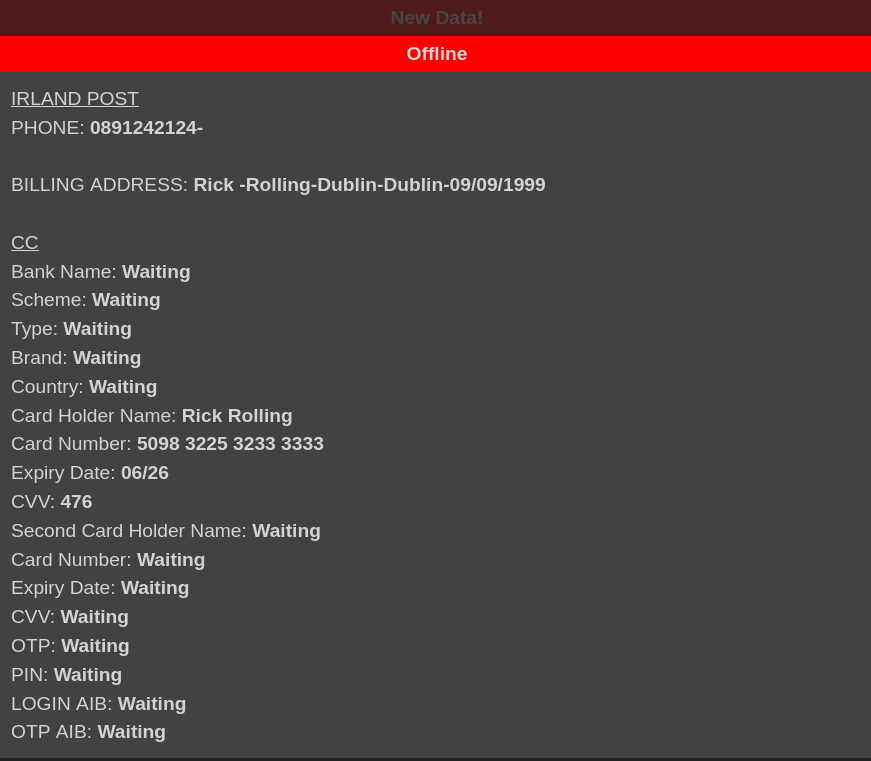
I was able to look for the dummy data which I entered during the initial investigation phase. The data get’s nicely categorized and presented to panel administrator for viewing. Also, there are other functionalities in the panel which allows administrator’s to request personal information or send fake bank OTPs directly to the victim’s phone number.
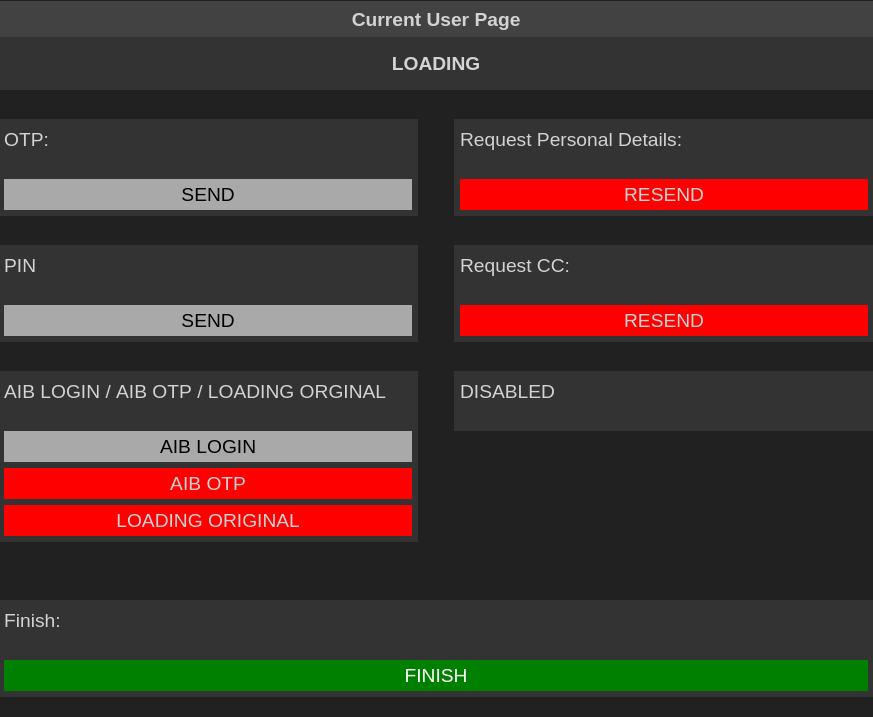
Final Words
Upon querying various threat intel services, I have found many similar domains which are utilizing this Contiinued phishing kit and actively targetting users to steal potential PII data. This phishing kit primarily masquerades as HSBC bank, An-Post and other bank portals which have their presence in UK and Europe.
Although, their setup looks pretty obvious and phishy but still the amount of data they harvest is huge. Security awareness and education on phishing attack vectors can help detect and prevent such type of attacks. It was fun analyzing and understanding the mechanics behind this phishing kit. Indeed a great learning experience…!
I kept the write up easy to read and follow up along without getting into more technical details as it might aware the operators about the bug they have in their portal and they might turn it into a robust one (we never know !). Although, this phishing kit seems quite old but it’s stil acitve. Latest versions of this kit has been seen lately in the public domain. If we get an opportunity, we will do the honors for that also!
That’s it for this one … see you folks in the next blog post ..! ❤️
 Namaste, I'm Saraunsh Shewale from India <3. I love to hack !. Going to blog about my research in infosec, writups of CTF challenges & HTB machines and occasional life lessons !!
Namaste, I'm Saraunsh Shewale from India <3. I love to hack !. Going to blog about my research in infosec, writups of CTF challenges & HTB machines and occasional life lessons !!