TCS HackQuest Season 5 | Round - 2 & 3
Hello again ! So here’s the writeup for round 2 & 3 of TCS HackQuest Season 5.
Round 2 was group discussion among 10 participants in each group. It was all about the approach taken to solve the CTF challegnes of round 1. Learnt lot from my fellow participants while we were discussing about every approach possible to solve the challenges.
Round 3 was proctored CTF round where we had to turn on the camera throughout the challenge duration. There were 3 CTF challenges & time duration was 2 hours. I managed to solve 2 and got 600 points.
After solving the CTF challenges we were given 1 hour to document everything we did to obtain the flag in a word document provided by TCS HackQuest team. So, make sure to write understandable descriptive steps that you have taken to solve the challenges & take screenshots of everything you do !!
I wrote this blog in a very beginner friendly way to help my future infosec buddies !
Following are the 2 challenges that I managed to solve in Round 3:
1. It’s Exposed !!
Flag: "hq5{50m3*pu811c}"
- This challenge was simple OSINT. As it was given in the challenge about company startup named – arcanehqdev. So, I ran simple google search with this keyword & got following results.
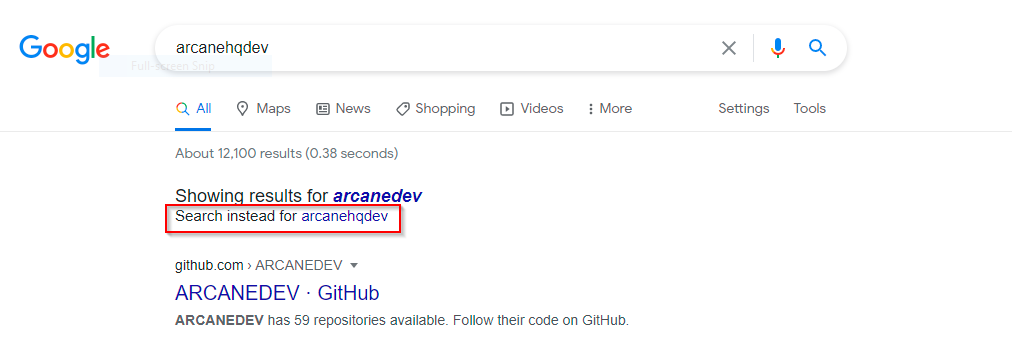
- Then click on search instead & it gives 2 URLs which are related to Trello boards. Clicking on first Trello board link gives:
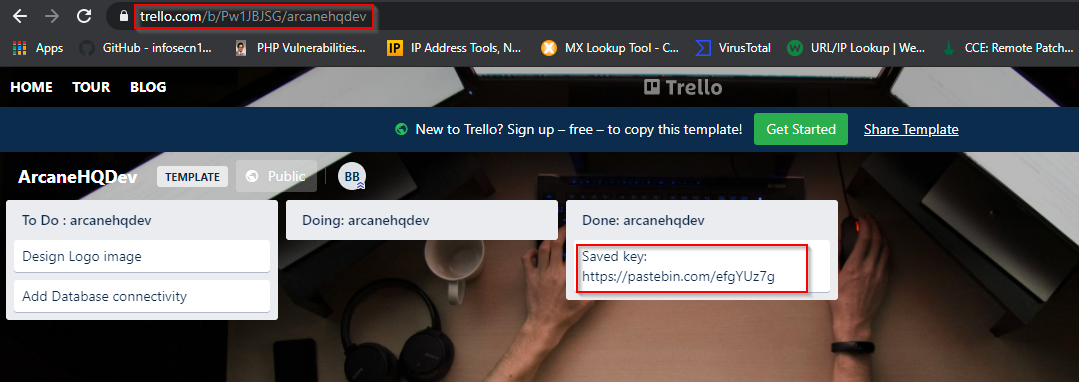
- As we can see there’s a pastebin link shared with description as: Saved key. So, I browsed the link & got the key.
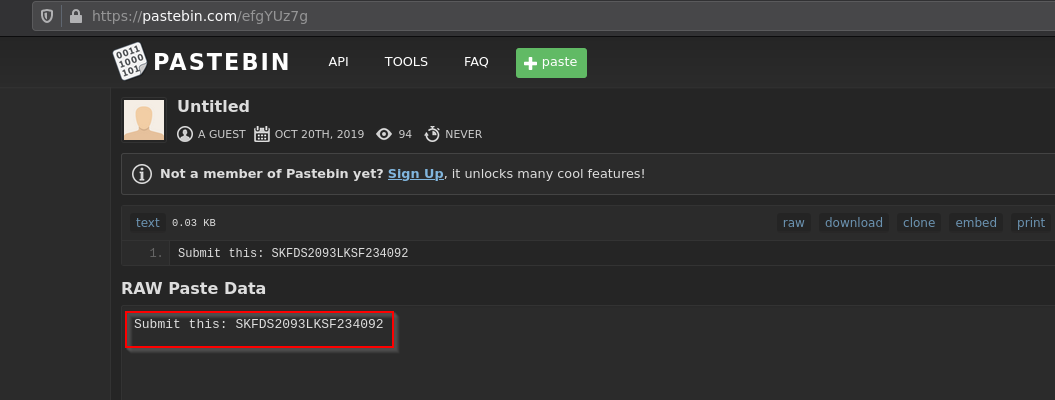
- Submitting this key into the challenge website link returns the flag.
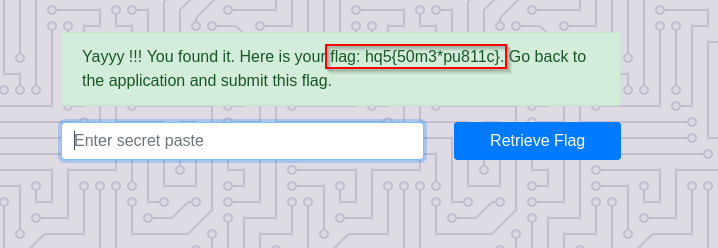
2. A Pandemic Inhibitor
Flag: "hq5{y0u_54v3d_y0u2531f}"
- We are given a website link, when we visit this link we see all sorts of guidelines and basic static info on the page regarding covid-19. Viewing the source code of the page, reveals a interesting API endpoint.
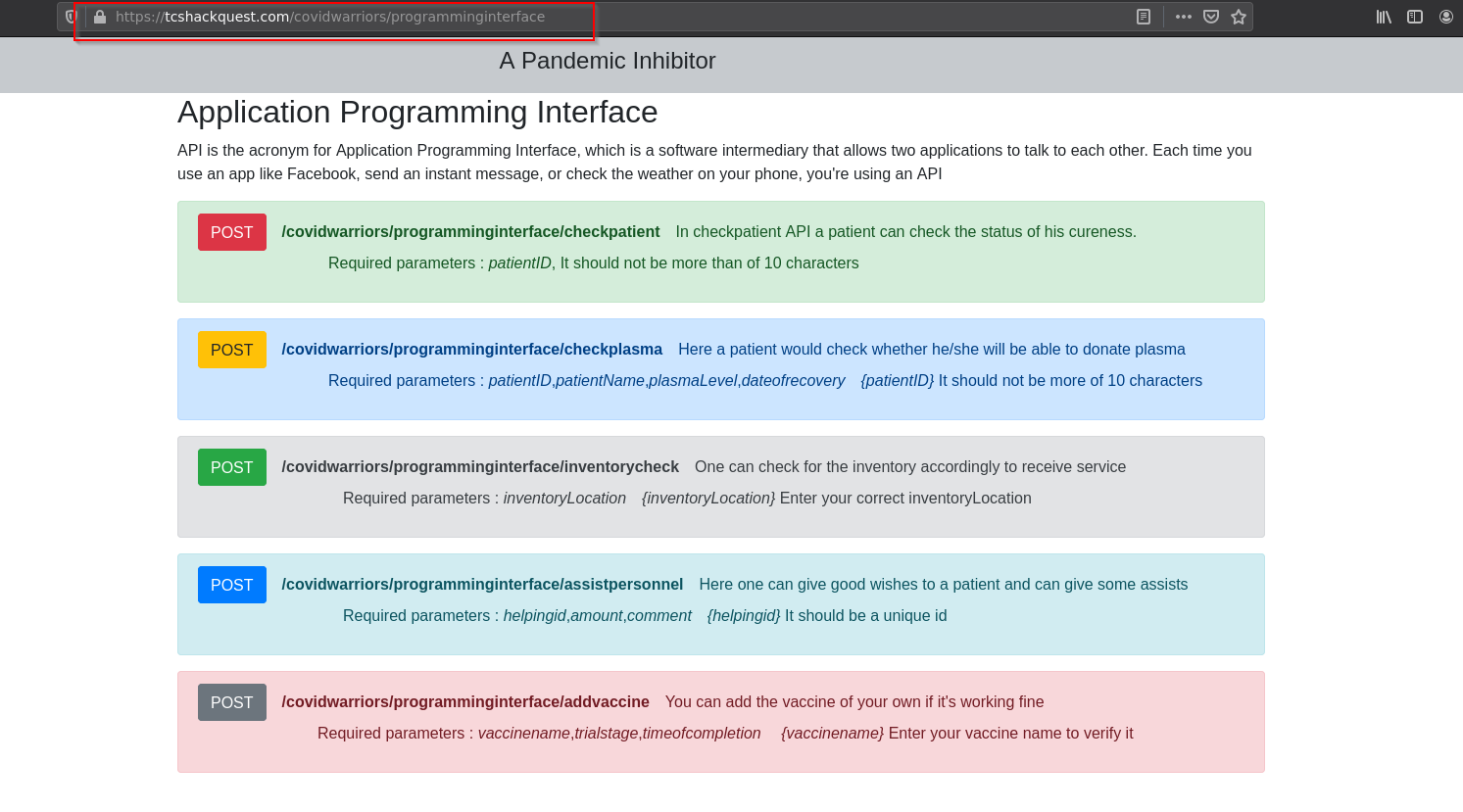
- When we visit this endpoint, we get the following API information that may present on the website along with the required parameters for each API call.
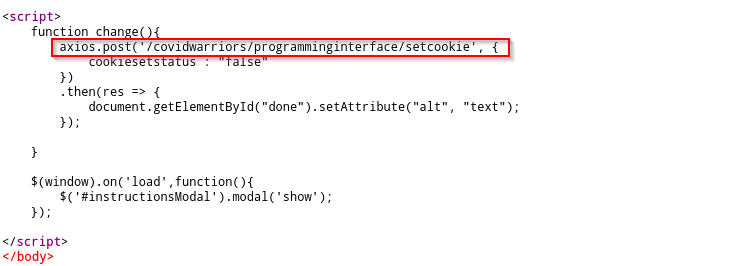
- Now I tried all the API requests with trial & error methdology and observed the responses in burp suite. The one which gave me the flag was API: assistpersonnel.
- Then I capture the request in burp suite, added all the required parameters – helpingid, amount & comment. When I sent this request, the response came in as Helping ID is not registered.
- Then I thought of inputting my DT ID which is used to login in the TCS portal inside the parameter helpingid and guess what I got the flag in response of api request.
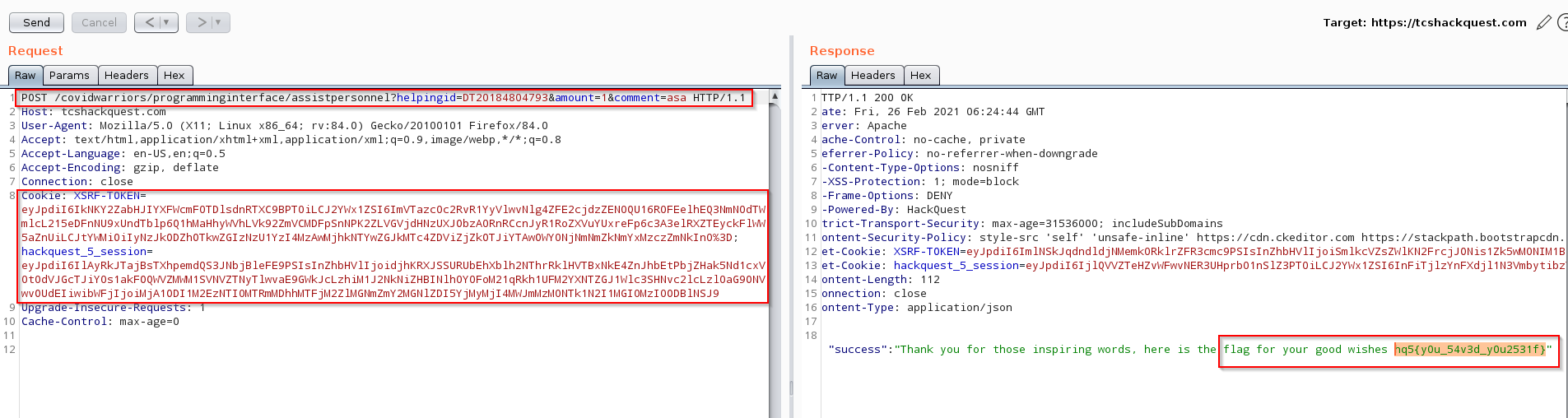
Gracias & all the best !!
 Namaste, I'm Saraunsh Shewale from India <3. I love to hack !. Going to blog about my research in infosec, writups of CTF challenges & HTB machines and occasional life lessons !!
Namaste, I'm Saraunsh Shewale from India <3. I love to hack !. Going to blog about my research in infosec, writups of CTF challenges & HTB machines and occasional life lessons !!